

After generating the required AWS credentials, you will need to enter them into the CloudEndure User ConsoleCloudEndure SaaS User Interface. A web-based UI for setting up, managing, and monitoring the Migration and Disaster Recovery solutions..
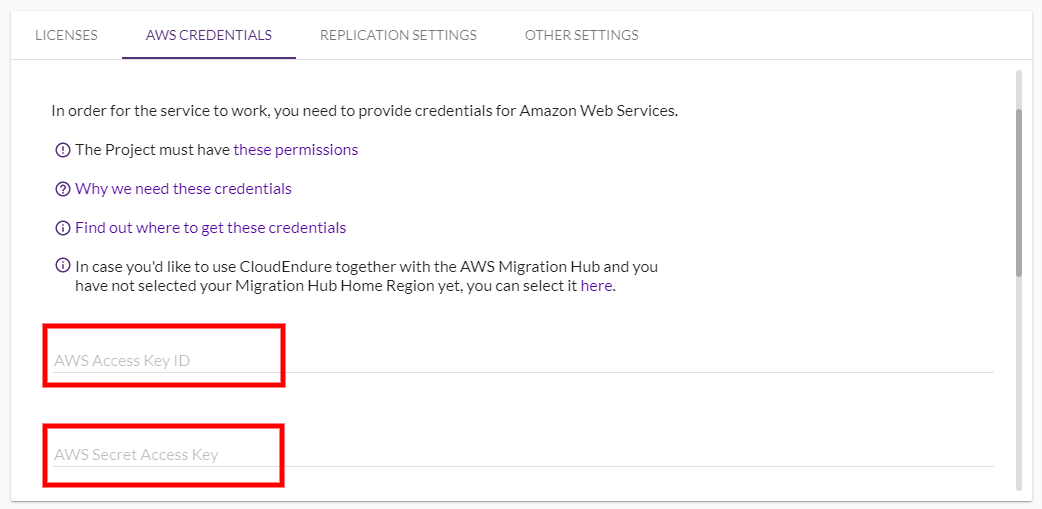
Note: Reminder, your AWS Access Key ID and AWS Secret Access Key can be found within the Download.csv file you downloaded after setting up your AWS credentials in the previous section.

Note: Click the EDIT button if you need to edit your Credentials. 
Note: If the AWS credentials you entered do not exist or invalid in any way, or if the IAM policy you created and attached to the user does not contain the required permissions, you will get the following error message: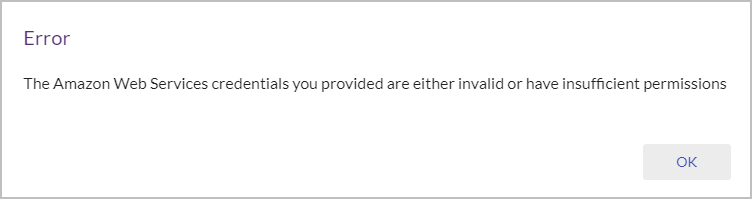
In this case, you can should attempt the following troubleshooting steps:
CloudEndure allows you to host your Replication ServersThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location. in the Staging AreaA part of the Target location; includes the Replication Servers’ subnet, IPs, and the Replication Servers and their disks. in one AWS AccountThe entity that signed up with CloudEndure. while launchingAfter the replication to the Staging area, launching is the process of setting up the Replication Servers, for Testing or Cutover and Recovery purposes. your replicated SourceThe location of the Source machine; Currently either a specific Region or Other Infrastructure. machines (which will become TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). machines after launch) in a separate TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). AWS AccountThe entity that signed up with CloudEndure..
This functionality is valuable if you have more than 300 servers and are being limited by the 300 installed servers per AWS AccountThe entity that signed up with CloudEndure. per AWS RegionA Region denotes a geographical area (US east, EU west, etc.). Each Region has multiple, isolated locations known as Zones. Zones are isolated from one another, but Zones within the same Region are connected through low-latency links. Cloud Regions exist in AWS, Microsoft Azure, and GCP. limit.
Important! When activating this feature you will only be able to select Other Infrastructure as your SourceThe location of the Source machine; Currently either a specific Region or Other Infrastructure. under the Replication Settings tab, and you will not be able to select a specific AWS SourceThe location of the Source machine; Currently either a specific Region or Other Infrastructure. RegionA Region denotes a geographical area (US east, EU west, etc.). Each Region has multiple, isolated locations known as Zones. Zones are isolated from one another, but Zones within the same Region are connected through low-latency links. Cloud Regions exist in AWS, Microsoft Azure, and GCP..
Important! Your TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). machines can only be launched in the same RegionA Region denotes a geographical area (US east, EU west, etc.). Each Region has multiple, isolated locations known as Zones. Zones are isolated from one another, but Zones within the same Region are connected through low-latency links. Cloud Regions exist in AWS, Microsoft Azure, and GCP. used for the Replication ServersThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location. as defined under the Replication Settings.
Important! For this feature to work, you will need to modify the CloudEndure IAM Policy for the TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). AWS AccountThe entity that signed up with CloudEndure.. Use the regular CloudEndure IAM Policy, and add the following line in between "ec2:DeleteSnapshot", and "ec2:ModifyVolumeAttribute",:
"ec2:ModifySnapshotAttribute",
Note: Customers that wish to enable Volume Encryption must share the share the KMS encryption key from the Target AWS Account with all Staging AWS Accounts. The default key cannot be shared. Learn more here.
Note: The Target AWS Account will use the same Blueprint settings as those defined in the Project.
To use a different AWS AccountThe entity that signed up with CloudEndure. to host your TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). machines, scroll down to the Target Account Credentials section on the AWS CREDENTIALS tab.
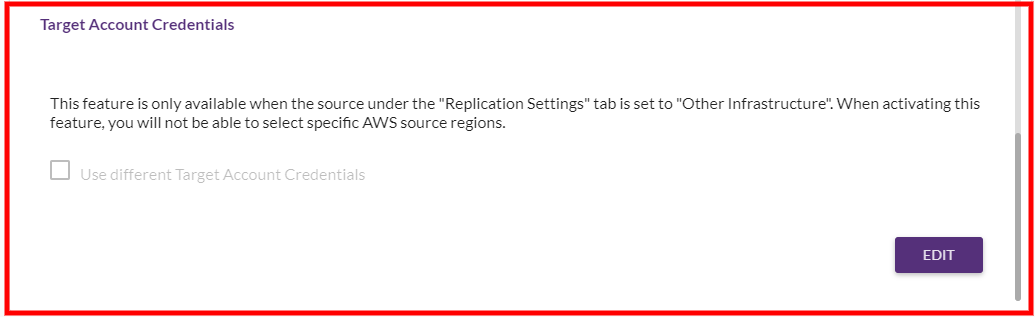
Click the EDIT button.

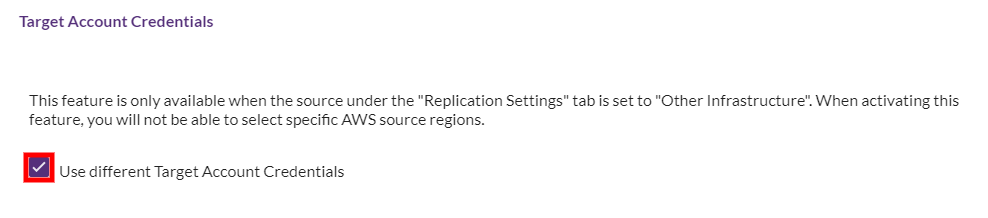
Check the Use different Target Account Credentials box.
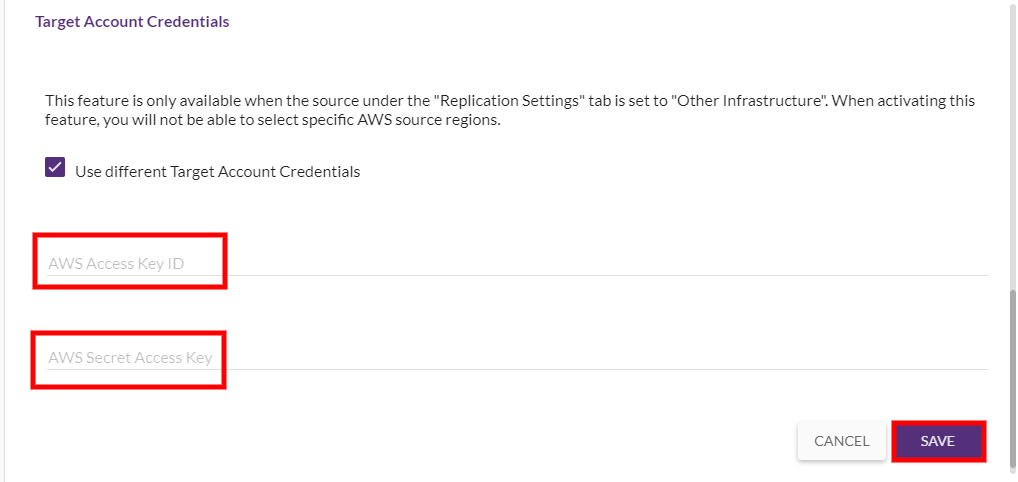
The AWS Access Key ID and AWS Secret Access Key fields will appear. Generate these credentials within your TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). AWS AccountThe entity that signed up with CloudEndure. by following the instructions in the Generating the Required AWS Credentials section and click SAVE.
©2020 COPYRIGHT CloudEndure - Terms of Service - Privacy Policy - AWS Vulnerability Reporting Guidelines - Report a Security Issue