
Generating the Required AWS Credentials
To generate the required AWS credentials to use with the CloudEndure , you need to create at least one AWS Identity and Access Management (IAM) user, and assign the proper permission policy to this user. You will obtain an Access key ID and a Secret access key, which are the credentials you need to enter into the CloudEndure .
Note: As per best practices for managing AWS access keys, you should rotate IAM keys periodically. Changing IAM keys will result in replication servers recycle resulting in a temporary lag.
For detailed explanations and instructions on the creation of IAM users, refer to the AWS documentation.
The instructions below describe the necessary steps for creating an IAM user with the required policy for CloudEndure credentials. These steps include the following:
- Creating a policy for the CloudEndure solution.
- Creating a new IAM user and generating AWS credentials
Creating a Policy for CloudEndure
The AWS policy you need to create for running CloudEndure solution is based on a pre-defined CloudEndure policy. This CloudEndure policy contains the necessary permissions for using AWS as your infrastructure.
Important! Do not change the permissions in the CloudEndure policy without consulting AWS support. Changing the policy permissions may prevent your CloudEndure solution from running.
To create an AWS policy for CloudEndure solution:
- Sign in to AWS Console with your AWS account.
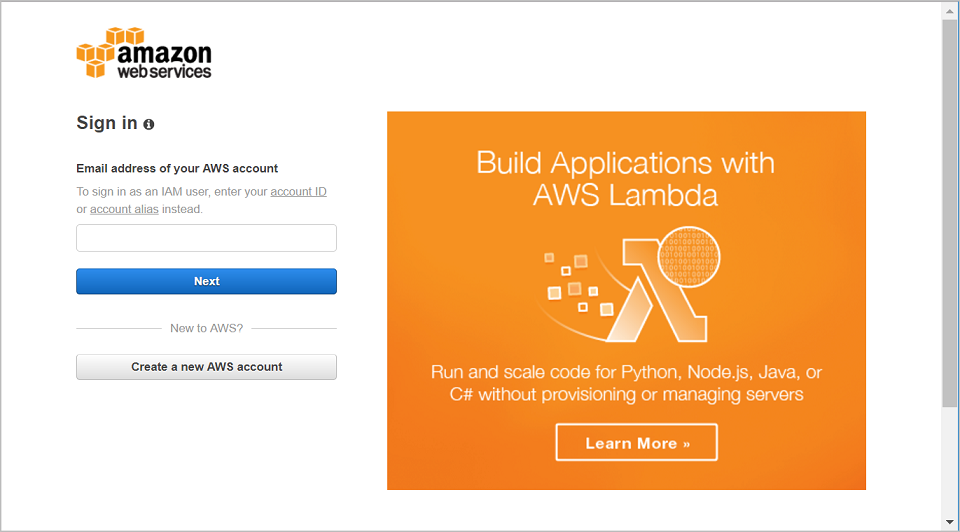
Note: If you do not have an AWS account, create an account by clicking the Create a new AWS account button.
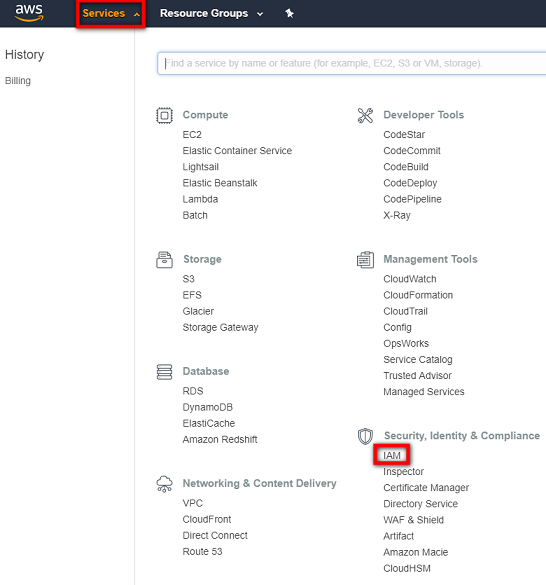
- In the AWS Console, click on Services and then navigate to Security, Identity & Compliance > IAM.
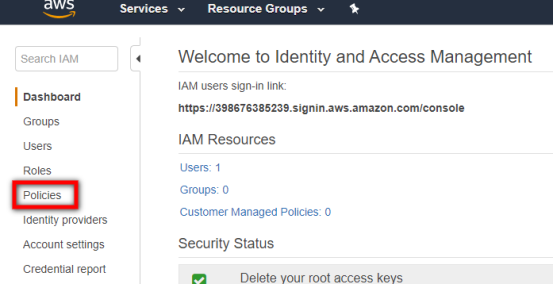
- On the Welcome to Identity and Access Management page, select the Policies option from the left-hand navigational menu.
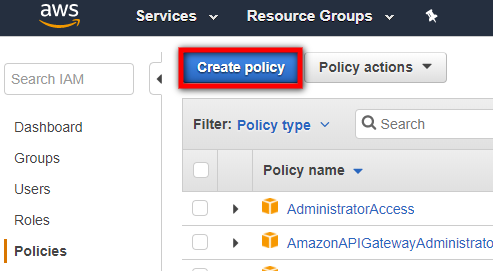
-
On the Policies page, click the Create policy button.
-
On the Create Policy page, click the JSON tab.
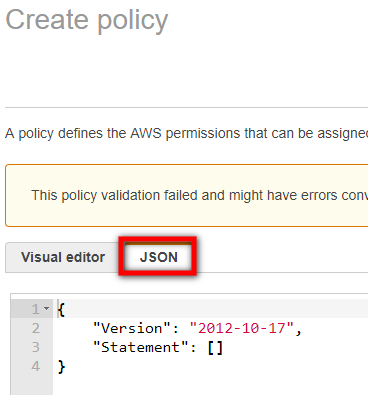
-
Navigate to the CloudEndure IAM Policy. Copy the policy code.
Note: Customers that are migrating into the AWS China region should copy the China IAM Policy code
- Paste the copied code into the JSON field. Paste the code over any text that currently exists in the field.
Note: Customers that want to launch Target machines with specified IAM Roles (that can be set through each machine's Blueprint) should manually add the iam:PassRole permission to the CloudEndure IAM Policy when entering the code into the AWS Console. The default IAM Policy provided by CloudEndure does not contain this permission.
Note: Customers that are using any GovCloud region as the Target should define the ARN within the IAM Policy as arn:aws-us-gov:ec2 instead of arn:aws:ec2
- Click on Review policy at the bottom right of the page.

- On the Review policy page, enter a name for the new AWS-CloudEndure policy in the Name field. Enter an optional description in the Description field.
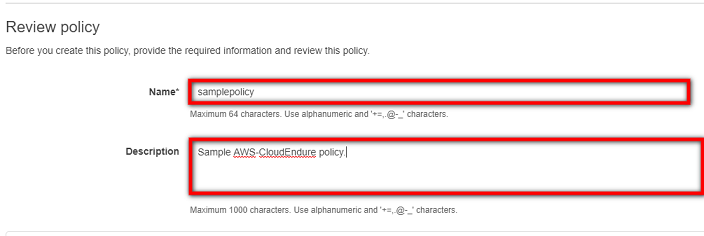
- Click the Create policy button at the bottom right of the page.

- You will be redirected back to the main Policies page and a confirmation stating that your new policy has been created will appear at the top of the page.
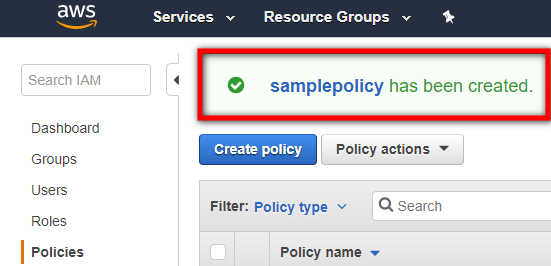
The next step is to create a new user, and then attach the policy you created to this user. During this procedure, you will be provided with an Access key ID and a Secret access key, which are the credentials you will need to enter into CloudEndure .
Creating a New IAM User and Generating AWS Credentials
After creating an AWS policy which is based on CloudEndure's pre-defined policy, you will need to create a new IAM user and to attach the new policy to this user. You also need to provide this user with a Programmatic access type to enable the use of the new policy. At the end of this procedure, you will be provided with an Access key ID and Secret access key. It is important to save these values in an accessible and secured location, since they are required for running your CloudEndure solution.
Creating a new IAM User and generating AWS credentials
- Navigate to Users on the left-hand navigational menu within IAM.
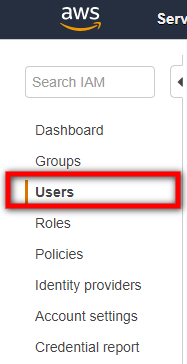
- Click on Add user.
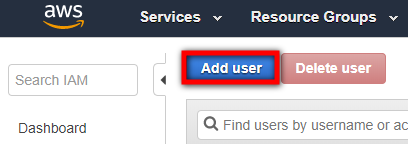
- On the Add user page, set the following:
- User name - add a username for the new user.
- Access type - check the Programmatic access option.
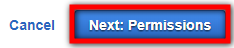
- Click Next: Permissions at the bottom right of the page.
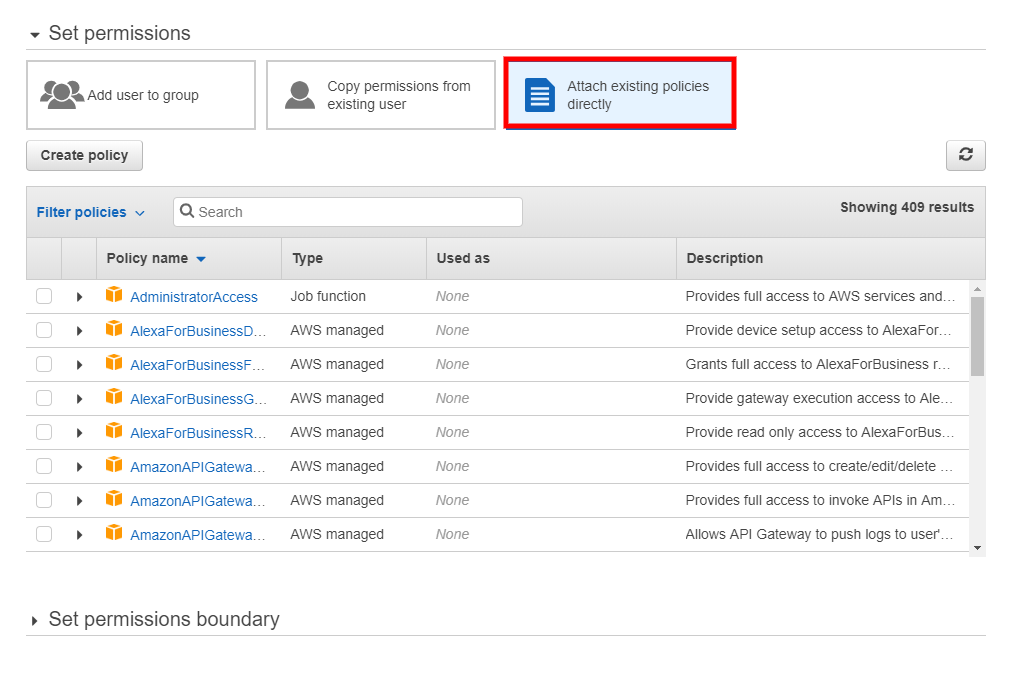
- On the Set permissions page, select the Attach existing policies directly option.
Note: If you already created a group or a user with the required CloudEndure permissions, you can use one of the two other options.
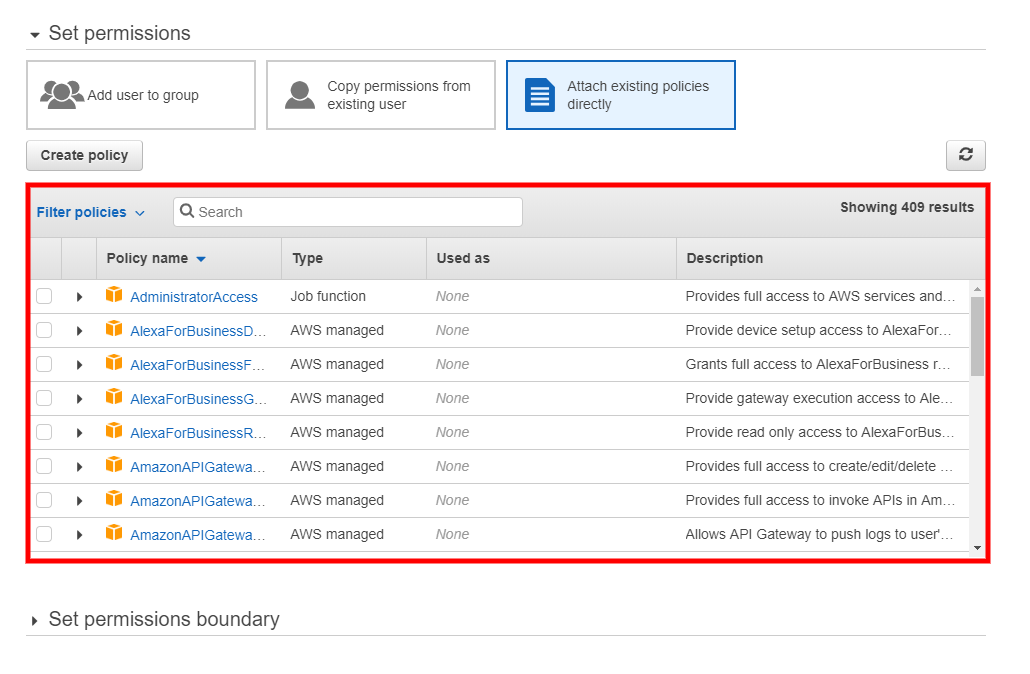
- Locate the policy you created in the previous Create a Policy for CloudEndure section. You can either search for the policy in the Search box or locate it manually by scrolling through the policy list.
-
Once you have located the policy, check the box next to it.
.png)
- Click the Next: Tags button at the bottom right of the page.
- You do not need to add any tags. Click the Next: Review button at the bottom right of the page

-
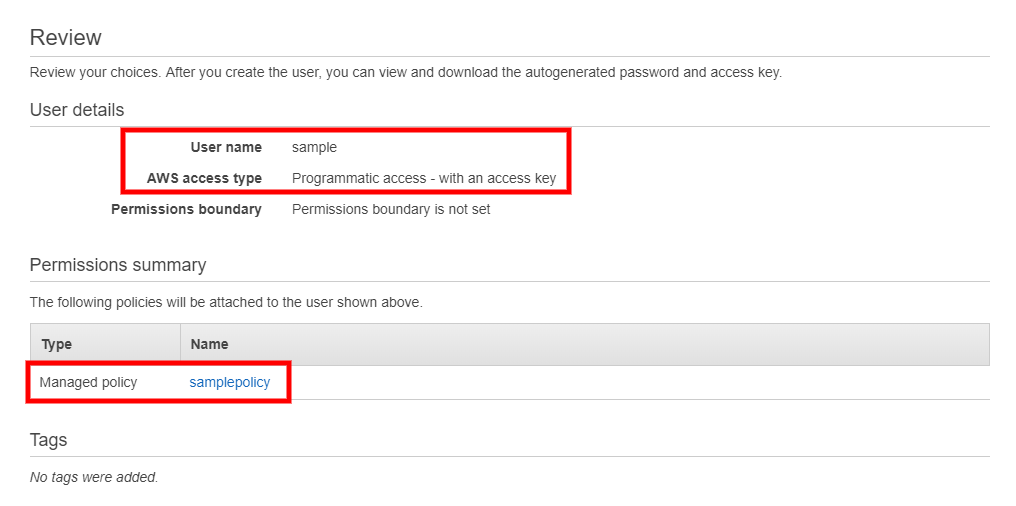
On the Review page, verify that the correct User name, AWS access type (Programmatic access), and Managed policy are selected.
- Click the Create User button at the bottom right of the page.
- A confirmation page will appear. This page provides you with your Access key ID and Secret access key which you will need to enter into the CloudEndure .
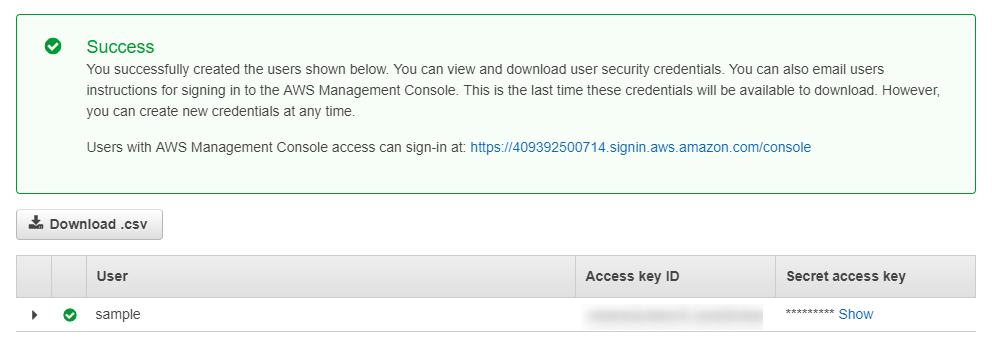
Click Show under Secret access key to see your key.
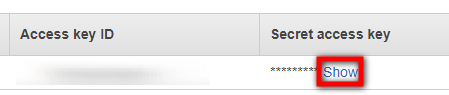
Important! You need the Access key ID and Secret access key to run your CloudEndure solution. You can save these keys in a separate file for easy access by clicking the Download.cvs button. Make sure to save these values in an accessible and secure location.
- Save your Access key ID and Secret access key. Then, to finish the procedure, click the Close button at the bottom right of the page.

-
You will be returned to the Users page, and the details of the new user you created will be shown.
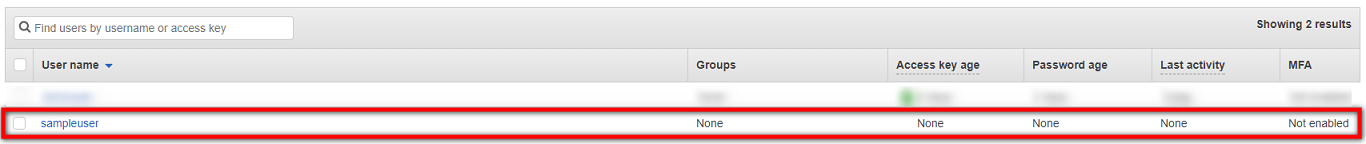
You have now completed the process of generating the required AWS credentials. The next step is entering your Access key ID and Secret access key into the CloudEndure .
©2020 COPYRIGHT CloudEndure - Terms of Service - Privacy Policy - AWS Vulnerability Reporting Guidelines - Report a Security Issue
















.png)








