
Use the CEDR to DRS Upgrade Assessment Tool and the Server Upgrade Tool to move your source servers from CloudEndure Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event. (CEDR) to AWS Elastic Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event. (DRS).
In general terms, the upgrade process includes 3 steps:
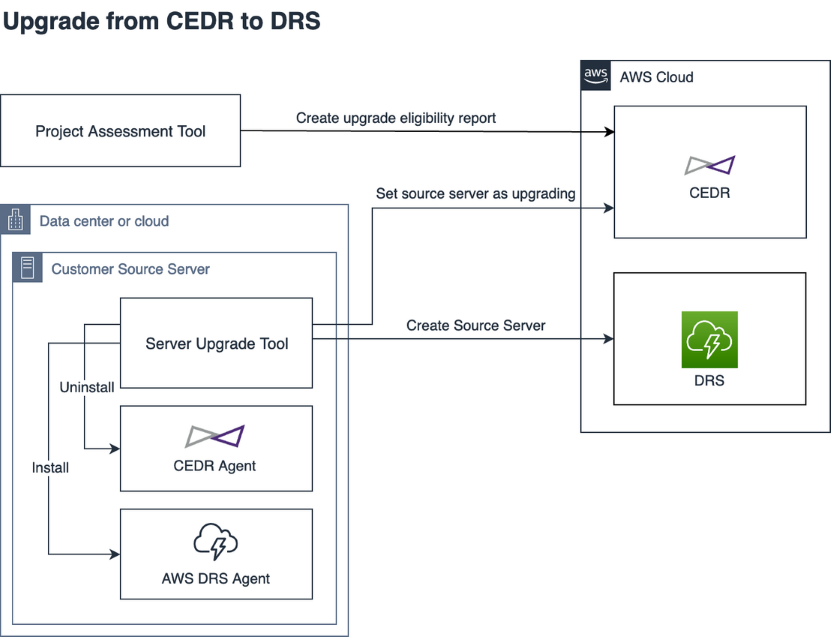
The following diagram outlines the upgrade process:

Learn how to upgrade by watching this 4-minute tutorial.
Only servers that have an OS that is supported by DRS and is not listed below can be upgraded using the upgrade tool. Servers with the following Operating Systems can only upgrade manually to DRS:
Windows
You must take the following steps before upgrading from CEDR to DRS:
The CloudEndure Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event. Upgrade Tool requires access to your AWS DRS environment to perform the migration of source servers and replication volumes. We recommend creating a new IAM Role for this access. However, you can also use an IAM User, as detailed below.
Note: Customers that are upgrading to any GovCloud region should define the ARN within the inline Policy as arn:aws-us-gov: instead of arn:aws:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"drs:DescribeSourceServers"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"drs:UpdateAgentSourcePropertiesForDrs",
"drs:GetLaunchConfiguration",
"drs:UpdateLaunchConfiguration",
"drs:BatchCreateVolumeSnapshotGroupForDrs",
"drs:GetReplicationConfiguration",
"drs:UpdateReplicationConfiguration"
],
"Resource": "arn:aws:drs:*:*:source-server/*"
},
{
"Effect": "Allow",
"Action": [
"ec2:DescribeLaunchTemplates",
"ec2:DescribeLaunchTemplateVersions",
"ec2:DescribeInstanceTypes",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeSnapshots"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "ec2:CreateSecurityGroup",
"Resource": "arn:aws:ec2:*:*:vpc/*"
},
{
"Effect": "Allow",
"Action": "ec2:CreateSecurityGroup",
"Resource": "arn:aws:ec2:*:*:security-group/*",
"Condition": {
"Null": {
"aws:RequestTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:ModifyLaunchTemplate",
"ec2:CreateLaunchTemplateVersion"
],
"Resource": "arn:aws:ec2:*:*:launch-template/*",
"Condition": {
"Null": {
"aws:ResourceTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:CreateTags",
"ec2:CopySnapshot"
],
"Resource": "arn:aws:ec2:*:*:snapshot/*",
"Condition": {
"Null": {
"aws:RequestTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:CreateTags",
"ec2:CopySnapshot"
],
"Resource": "arn:aws:ec2:*:*:security-group/*",
"Condition": {
"Null": {
"aws:RequestTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"kms:CreateGrant"
],
"Resource": "*"
}
]
}{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"kms:DescribeKey"
],
"Resource": "{CMK_ARN}",
"Effect": "Allow"
}
]
}aws sts assume-role --role-arn arn:aws:iam::12345678910:role/CEDRUpgradeRole --role-session-name CEDRUpgradeSession
Example Response Body
"CredentialsAccount login information, including the Username and Password.": { "AccessKeyId": "ASIA5RYJEKN6BCAFP5JF", "SecretAccessKey": "HuKE3h2y9iQS9sjnIjI1IxA82T/+2Qw59jPDIVq0", "SessionToken": "IQoJb3JpZ2luX2VjEAgaCXVzLXdlc3QtMiJIMEYCIQCkhBseWi7CjSRyLHiu835DFzJQd/nloh9AqF2PmjwJQwIhAPzertEUNEGmtv11Mq5wHW401uoOZEf+uca7gp6VFQ3sKqgCCLH//////////wEQABoMOTMxNDkwMTkwMjA0IgwkjXN1B6/PjrTjcKUq/AG9nSkOmJnMqsCBQpcje/naHEq9aIVknK0ffVmS+RRKiU0JGXO19f+5gSlE1T1JjBH0Sn8cs+WjMjVQTO0slznoBjOAK6QSDJw5EZCTv3fIUcU3Rz2A3Zn+T4OIRh/GhWtoW+9j/i9YgstrhcK+Ts7SqxlinOYFChlBjJx7NhHLTtDL7UN7s3g6CkSuO/9bXfA7UaBy8IQof/UCQYJ27VF7PzwhMqBTWkRHzu6fu+a0XLmT08oO7TUfOSvTNc6d3Zu4xFIZpHNU9CH8OSexd5ZXf3VGdvobHqUWa7PukhB27hvtc4qE6jGrgAgtyS8ZpAKHe9jCDKF+uxyGceQwleSEoAY6nAGCjMapNUd5+mFtVxVtuW4r7XSXwaR4OauqE4K5VgTjATbEAo+KaDpceUwLB6VZYYGwclt3tdRO+y9ENqkiznwm5K30pVQW++0dqJu1AnWYieJr+vNBeYnzxxf7VbcQLIVr7cDrGX+JTK8r0UMsS+hR1U4UJEwNNpBD4bwJ/Vgno1mEGC85vhaTHwdsvWyPnuXV2rVOKdPYYoFa/HA=", "Expiration": "2023-03-03T00:32:37+00:00" }, "AssumedRoleUser": { "AssumedRoleId": "AROA5RYJEKN6HKYJ3BIKE:CEDRUpgradeSession", "Arn": "arn:aws:sts::12345678910:assumed-role/CEDRUpgradeRole/CEDRUpgradeSession" }
Note that whenever possible, it is advisable to create an IAM role rather than an IAM user.
Use the existing policy AWSElasticDisasterRecoveryAgentInstallationPolicy and manually attach it to the user.
Create an additional internal policy with the following value:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"drs:DescribeSourceServers"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"drs:UpdateAgentSourcePropertiesForDrs",
"drs:GetLaunchConfiguration",
"drs:UpdateLaunchConfiguration",
"drs:BatchCreateVolumeSnapshotGroupForDrs",
"drs:GetReplicationConfiguration",
"drs:UpdateReplicationConfiguration"
],
"Resource": "arn:aws:drs:*:*:source-server/*"
},
{
"Effect": "Allow",
"Action": [
"ec2:DescribeLaunchTemplates",
"ec2:DescribeLaunchTemplateVersions",
"ec2:DescribeInstanceTypes",
"ec2:DescribeSecurityGroups",
"ec2:DescribeSubnets",
"ec2:DescribeSnapshots"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "ec2:CreateSecurityGroup",
"Resource": "arn:aws:ec2:*:*:vpc/*"
},
{
"Effect": "Allow",
"Action": "ec2:CreateSecurityGroup",
"Resource": "arn:aws:ec2:*:*:security-group/*",
"Condition": {
"Null": {
"aws:RequestTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:ModifyLaunchTemplate",
"ec2:CreateLaunchTemplateVersion"
],
"Resource": "arn:aws:ec2:*:*:launch-template/*",
"Condition": {
"Null": {
"aws:ResourceTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:CreateTags",
"ec2:CopySnapshot"
],
"Resource": "arn:aws:ec2:*:*:snapshot/*",
"Condition": {
"Null": {
"aws:RequestTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"ec2:CreateTags",
"ec2:CopySnapshot"
],
"Resource": "arn:aws:ec2:*:*:security-group/*",
"Condition": {
"Null": {
"aws:RequestTag/AWSElasticDisasterRecoveryManaged": "false"
}
}
},
{
"Effect": "Allow",
"Action": [
"kms:CreateGrant"
],
"Resource": "*"
}
]
}{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"kms:DescribeKey"
],
"Resource": "{CMK_ARN}",
"Effect": "Allow"
}
]
}
Follow the instructions in this guide to quickly run the CEDR to DRS Upgrade Assessment Tool and Server Upgrade Tool on Linux or Windows without any additional parameters.
1. Download the Assessment Tool using the following command:
wget https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_assessment_tool
2. Match the Assessment Tool with your CloudEndure account and run the tool through the following command, once per CEDR project:
chmod +x cloudendure_to_drs_upgrade_assessment_tool
sudo ./cloudendure_to_drs_upgrade_assessment_tool --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0
3. Run the Server Upgrade Tool locally on each validated source server using the following command. Note that you must match the tool with your CloudEndure account and ProjectA Project is the basic organizational unit for running a CloudEndure solution. as well as the IAM credentials you created in the perquisites.
wget https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_tool
chmod +x cloudendure_to_drs_upgrade_tool
sudo ./cloudendure_to_drs_upgrade_tool start-upgrade --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX –-import-replication-configuration -–import-blueprint -–import-test-snapshot
4. Run the finalize-upgrade command:
sudo ./cloudendure_to_drs_upgrade_tool finalize-upgrade --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX
1. Download the Assessment Tool from the following URL:
https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_assessment_tool.exe
2. Match the Assessment Tool with your CloudEndure account and run the tool through the following command:
.\cloudendure_to_drs_upgrade_assessment_tool.exe --api-tokenXXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0
3. Download and run the Server Upgrade Tool locally on each validated source server using the following command. Note that you must match the tool with your CloudEndure account and ProjectA Project is the basic organizational unit for running a CloudEndure solution. as well as the IAM credentials you created in the perquisites.
https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_tool.exe
.\cloudendure_to_drs_upgrade_tool.exe start-upgrade --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX --import-replication-configuration –-import-blueprint –-import-test-snapshot
4. Run the finalize-upgrade command:
.\cloudendure_to_drs_upgrade_tool.exe finalize-upgrade --api-token --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX
The CEDR to DRS Upgrade Assessment Tool (also known as "the Assessment Tool") analyzes the ProjectA Project is the basic organizational unit for running a CloudEndure solution. to determine which servers are eligible for upgrade to DRS based on:
The Assessment Tool can be run on any Linux or Windows source machineThe computer, physical or virtual machine that needs to be protected by replication (Disaster Recovery) or migrated (Migration) The CloudEndure Agent is installed on the Source machine. that has connectivity to the CloudEndure Console. The following are instructions for downloading and running the Assessment Tool on both Linux and Windows.
wget https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_assessment_tool
chmod +x cloudendure_to_drs_upgrade_assessment_tool
You must match the Assessment Tool with your CloudEndure account through either using the API token or your account username and password and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID by running the sudo ./cloudendure_to_drs_upgrade_assessment_tool command. You can also use additional command line arguments to limit the scope of the Assessment Tool to exclude specific machines by ID or to only include specific machines by ID. The following parameters can be used:
--api-token - The CEDR api token --username - The CEDR username--password - The CEDR password--project-name - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. name. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. --project-id - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. uuid. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. --machine-ids - A list of machines to validate by uuid. If no value is provided, then all of the machines in the ProjectA Project is the basic organizational unit for running a CloudEndure solution. will be validated.--exclude-machine-ids - A list of machines by uuid to exclude from validation. The following is an example of running the Assessment Tool with the API token and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID:
sudo ./cloudendure_to_drs_upgrade_assessment_tool --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0
The following is an example of running the Assessment Tool with the username and password and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID:
sudo ./cloudendure_to_drs_upgrade_assessment_tool --username user@cloudendure.com --password my_secret_password --project-id 12345xx-0000-0000-0000-00aa00ab00b0
https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_assessment_tool.exe
.\cloudendure_to_drs_upgrade_assessment_tool.exe command. You can also use additional command line arguments to limit the scope of the Assessment Tool to exclude specific machines by ID or to only include specific machines by ID.The following parameters can be used:
--api-token - The CEDR api token --username - The CEDR username--password - The CEDR password--project-name - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. name. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided.--project-id - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. uuid. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided.--machine-ids - A list of machines to validate by uuid. If no value is provided, then all of the machines in the ProjectA Project is the basic organizational unit for running a CloudEndure solution. will be validated.--exclude-machine-ids - A list of machines by uuid to exclude from validation. The following is an example of running the Assessment Tool with the API token and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID:
.\cloudendure_to_drs_upgrade_assessment_tool.exe --api-tokenXXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0
After you run the Assessment Tool, it will connect to the CloudEndure Console and will validate the CloudEndure ProjectA Project is the basic organizational unit for running a CloudEndure solution. for DRS eligibility.
The Assessment Tool will scan the machines in your CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. and will determine their eligibility status for upgrade to DRS. The eligibility will be determined according to the following information:
Once the assessment is complete, the Assessment Tool will display the assessment results, including which machines are:
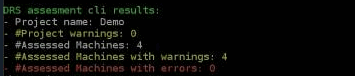
Validation warnings may be caused by the following:
Validation errors mean that the machineA physical or virtual computer. has a configuration which is not supported by DRS and cannot be upgraded. Currently, the only validation errors are an unsupported machineA physical or virtual computer. OS and an unsupported AWS RegionA Region denotes a geographical area (US east, EU west, etc.). Each Region has multiple, isolated locations known as Zones. Zones are isolated from one another, but Zones within the same Region are connected through low-latency links. Cloud Regions exist in AWS, Microsoft Azure, and GCP..
The Assessment Tool will create a folder in the same directory where the tool was installed called output. There, you will find a CSV that lists all the warnings, errors, and mitigations. 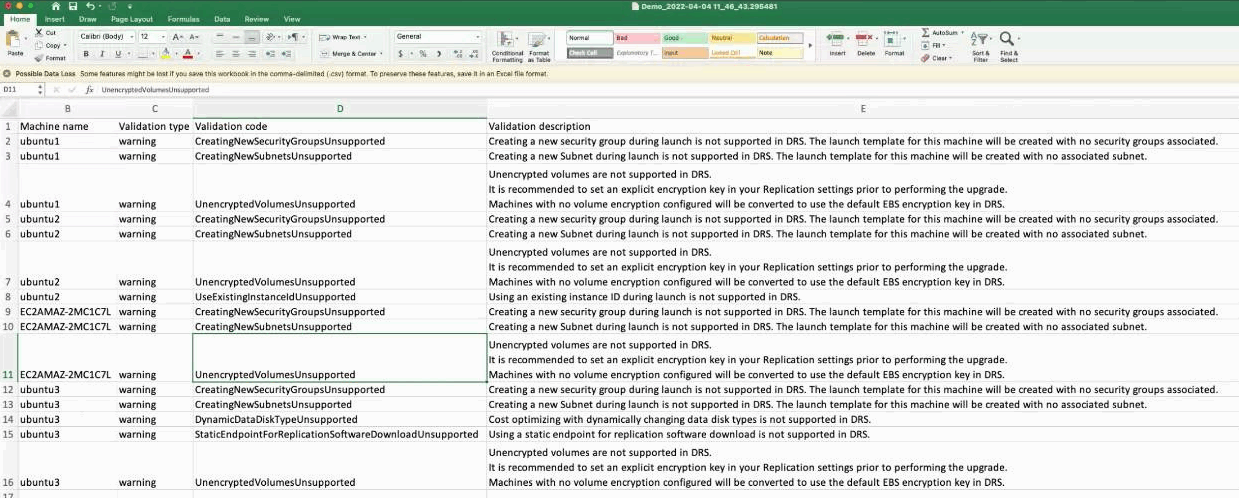
After you decide which machines you want to upgrade to DRS and mitigate all the relevant warnings and errors, use the Server Upgrade Tool to perform the upgrade.
The Server Upgrade Tool will upgrade the server, including importing the machineA physical or virtual computer. configuration from CEDR to DRS, importing a consistent snapshot from CEDR to DRS, and replacing the CEDR agentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. with the AWS Replication AgentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location.. You will be able to launch a Drill or Recovery instance for the server in DRS to verify that the server launches correctly prior to uninstalling the CEDR agentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. from the server.
You must run the Server Upgrade Tool locally on each validated source server.
The tool has two distinct steps:
During the start-upgrade step, the server's DRS configuration will be validated and copied without interrupting the server's protection. The tool will perform the following:
Note: This step may identify new warnings and errors that may not have been identified by the Assessment Tool, such as OS and architecture mismatches.
Important: You will be double billed between the time you run start-upgrade and finalize-upgrade. You will be billed for the source server and for the snapshot in DRS. Once finalize-upgrade is completed, the server is marked as Upgrading in CEDR and you will only be charged in DRS. Once the upgrade has been finalized, you can retain your CEDR source machineThe computer, physical or virtual machine that needs to be protected by replication (Disaster Recovery) or migrated (Migration) The CloudEndure Agent is installed on the Source machine. in the CloudEndure Console in order to have older PITPoint In Time recovery. The ability to restore a Machine to its state in one of the many Points In Time in the past (a feature related to DR). recoverability with no CEDR license charge.
Note: Run the Server Upgrade Tool as a sudo user in Linux.
You must run the Server Upgrade Tool on every source server you want to upgrade.
Note: The source server must have connectivity to both AWS and the CloudEndure Management Console.
Input the following command to download the Server Upgrade Tool:
wget https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_tool
To run the Server Upgrade Tool:
chmod +x cloudendure_to_drs_upgrade_tool
sudo ./cloudendure_to_drs_upgrade_tool start-upgrade command
You must match the Server Upgrade Tool with
The following parameters can be used:
Note: Use the --import-blueprint, --import-replication-configuration, and --import-test-snapshot flags if you want to import the server's blueprint, replication configuration, and/or launchable snapshot into DRS.
Important: If the --import-test-snapshot flag is not specified during the upgrade, a full sync of the source server will occur after finalize-upgrade is run. If the flag is specified during the upgrade, a rescan of the source server will occur after finalize-upgrade is run.
--api-token - The CEDR api token
--username - The CEDR username
--password - The CEDR password--project-name - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. name. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. --project-id - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. uuid. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. --aws-access-key-id - The AWS access key ID.--aws-secret-access-key -The AWS secret access key.--aws-session-token -The AWS session token. --import-replication-configuration - if set, the replication configuration will be copied from CEDR to DRS.--import-blueprint - if set, the Blueprint will be copied from CEDR to DRS.--import-test-snapshot - if set, import a launchable snapshot from CEDR to DRS in order to perform a Drill instance launch.--ignore-validation-warnings - Ignore warnings about machineA physical or virtual computer. configuration support in DRS.--ignore-validation-errors - Ignore errors about machineA physical or virtual computer. configuration support in DRS.--no-prompt - enable unattended execution.The following is an example of running the Server Upgrade Tool with the API token and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID, with the --import-blueprint, --import-replication-configuration, and --import-test-snapshot flags being used.
sudo ./cloudendure_to_drs_upgrade_tool start-upgrade --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX --import-blueprint --import-replication-configuration --import-test-snapshot
Note: Run the Server Upgrade Tool as an admin user in Windows.
You must run the Server Upgrade Tool on every source server you want to upgrade.
Note: The source server must have connectivity to both AWS and the CloudEndure Management Console.
https://cedr-to-drs-upgrade-tool.cloudendure.com/latest/cloudendure_to_drs_upgrade_tool.exe
.\cloudendure_to_drs_upgrade_tool.exe start-upgrade command. You must match the Server Upgrade Tool with:The following parameters can be used:
Note: Use the --import-blueprint, --import-replication-configuration, and --import-test-snapshot flags if you want to import the server's blueprint, replication configuration, and/or launchable snapshot into DRS.
Important: If the --import-test-snapshot flag is not specified during the upgrade, a full sync of the source server will occur after finalize-upgrade is run. If the flag is specified during the upgrade, a rescan of the source server will occur after finalize-upgrade is run.
--api-token - The CEDR api token
--username - The CEDR username
--password - The CEDR password--project-name - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. name. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. --project-id - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. uuid. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided.--aws-access-key-id - The AWS access key ID.--aws-secret-access-key -The AWS secret access key.--aws-session-token -The AWS session token. --import-replication-configuration - if set, the replication configuration will be copied from CEDR to DRS.--import-blueprint - if set, the Blueprint will be copied from CEDR to DRS.--import-test-snapshot - if set, import a launchable snapshot from CEDR to DRS in order to perform a Drill instance launch.--ignore-validation-warnings - Ignore warnings about machineA physical or virtual computer. configuration support in DRS.--ignore-validation-errors - Ignore errors about machineA physical or virtual computer. configuration support in DRS.--no-prompt - enable unattended execution.The following is an example of running the Server Upgrade Tool with the API token and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID, with the --import-blueprint, --import-replication-configuration, and --import-test-snapshot flags being used.
.\cloudendure_to_drs_upgrade_tool.exe start-upgrade --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX --import-blueprint --import-replication-configuration --import-test-snapshot
The Server Upgrade Tool will connect to the CloudEndure Console and perform validation. Once validation is complete, the tool will identify volumes for replication and the AWS Replication AgentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. will be installed with replication disabled without uninstalling the CEDR agentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location., so that your replication and disaster recovery operations are not disturbed in CEDR.
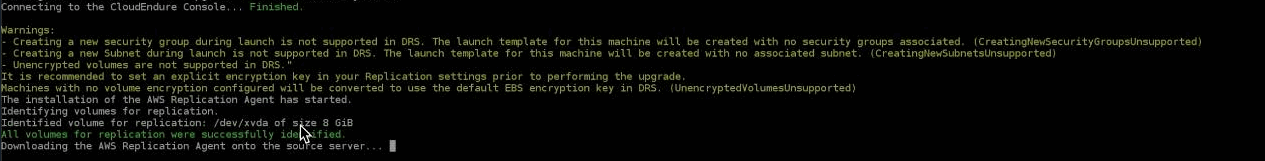
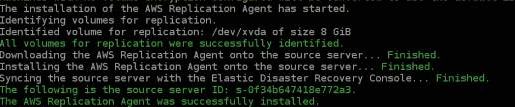
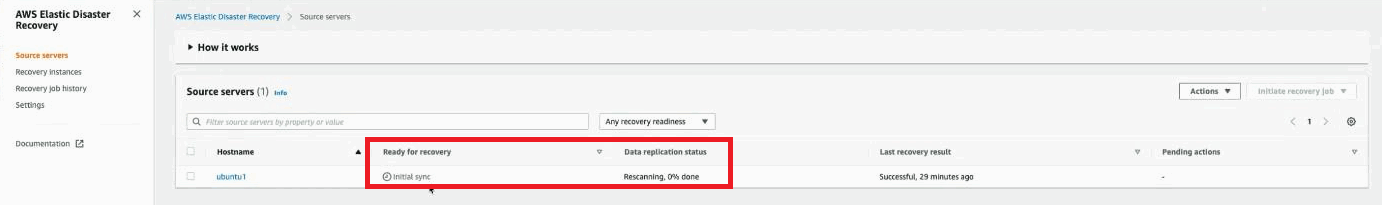
Once installation is complete, you will see the machineA physical or virtual computer. being added to DRS on the Source servers page.
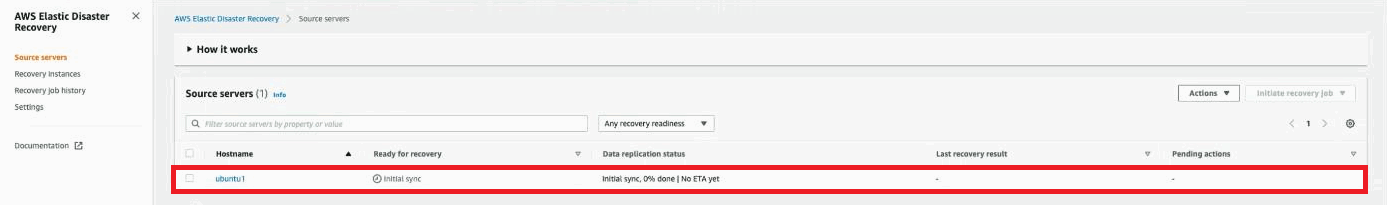
A consistent snapshot of the source server will be copied into DRS, allowing you to launch a Drill instance in DRS for the newly added source server.
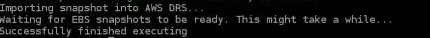
Once the snapshot has been added, the source server will display the Ready for recovery status in DRS.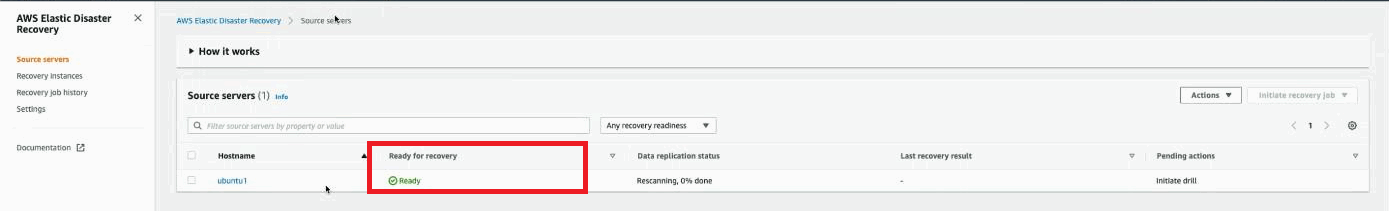
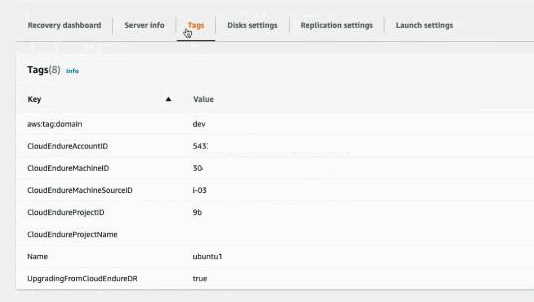
The following tags will also be added to the source server in DRS.
You will now be able to launch a Drill instance from the snapshot for the source server. Learn more about launching Drill instances in DRS.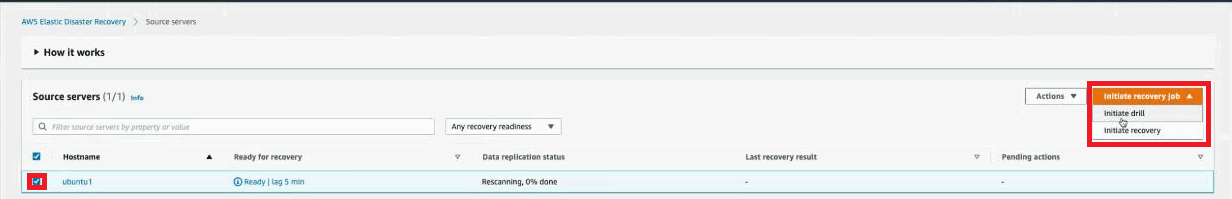
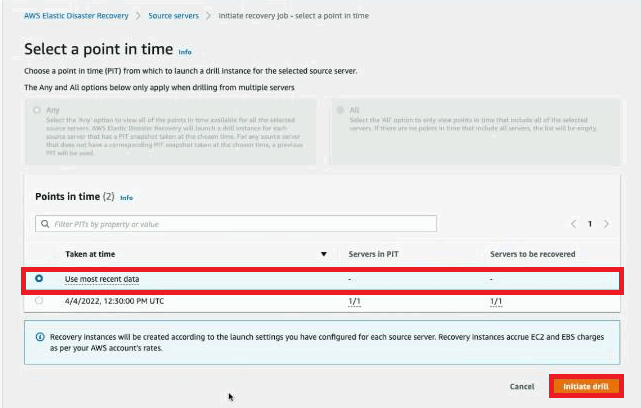
Note: In some scenarios, during the start-upgrade stage, DRS cannot identify the protected server's private IP and the option to copy private IP cannot be set to Yes. This does not happen during the finalize-upgrade stage.
Note: It will take a while for the PIT to appear, but you can launch from Use most recent data snapshot. You will not see any other PIT because the agent is still not actively replicating in DRS.
You will see the launched Drill instance on the Recovery instances page in DRS. TestThe same for Migration and Disaster Recovery. A process that is initiated manually. Launches Target machines on the Target location, and marks the tested machines on the Console as ready for Live Migration/Disaster Recovery. It is recommended to initiate a Test after the initial replication is completed. When a Test is initiated, an updated snapshot is created on the Staging Aaea. From this snapshot, a disk is created. your server's connectivity and make sure it works as required. If there are any issues, review your settings, change your blueprint, and perform the necessary troubleshooting steps. Once your tests are completed successfully, move on to the finalize-upgrade step.
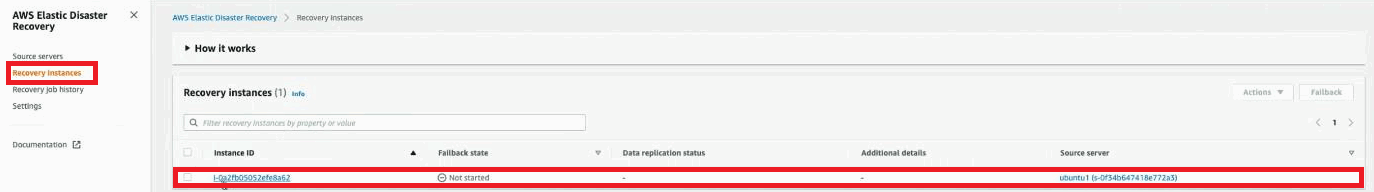
Once you have completed the start-upgrade steps and launched a Drill instance in DRS to validate that the server has launched successfully, finalize the upgrade through the finalize-upgrade command.
The Server Upgrade Tool will:
upgrading state. This new state will prevent you from being billed twice for DRThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event. in CEDR and DRS, and allow you to still launch PITPoint In Time recovery. The ability to restore a Machine to its state in one of the many Points In Time in the past (a feature related to DR). snapshots in CEDR.You must match the Server Upgrade Tool with:
Enter the following prompt to run the cloudendure_to_drs_upgrade_tool finalize-upgrade command.
The following parameters can be used:
--api-token - The CEDR api token
--username - The CEDR username
--password - The CEDR password--project-name - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. name. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. If none are provided, you will be prompted to select a ProjectA Project is the basic organizational unit for running a CloudEndure solution. from your account.--project-id - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. uuid. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. If none are provided, you will be prompted to select a ProjectA Project is the basic organizational unit for running a CloudEndure solution. from your account.--aws-access-key-id - The AWS access key ID.--aws-secret-access-key -The AWS secret access key.--aws-session-token -The AWS session token. The following is an example of running the Server Upgrade Tool finalize-upgrade command with the API token and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID.
sudo ./cloudendure_to_drs_upgrade_tool finalize-upgrade --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX
Enter the following prompt to run the .\cloudendure_to_drs_upgrade_tool.exe finalize-upgrade command.
The following are all of the parameters that can be used:
--api-token - The CEDR api token
--username - The CEDR username
--password - The CEDR password--project-name - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. name. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. If none are provided, you will be prompted to select a ProjectA Project is the basic organizational unit for running a CloudEndure solution. from your account.--project-id - The CEDR ProjectA Project is the basic organizational unit for running a CloudEndure solution. uuid. Only a single ProjectA Project is the basic organizational unit for running a CloudEndure solution. name or ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID can be provided. If none are provided, you will be prompted to select a ProjectA Project is the basic organizational unit for running a CloudEndure solution. from your account.--aws-access-key-id - The AWS access key ID.--aws-secret-access-key -The AWS secret access key.--aws-session-token -The AWS session token. The following is an example of running the Server Upgrade Tool finalize-upgrade command with the API token and the ProjectA Project is the basic organizational unit for running a CloudEndure solution. ID.
.\cloudendure_to_drs_upgrade_tool.exe finalize-upgrade --api-token --api-token XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX-XXXX --project-id 12345xx-0000-0000-0000-00aa00ab00b0 --aws-access-key-id AKIASXXXXXXXXXX --aws-secret-access-key XXXXXXXXXXXXXXXX --aws-session-token XXXXXXXXXXXXXXXX
The Server Upgrade Tool will connect to the CloudEndure Console and import the source server snapshot into DRS.
A rescan will be triggered, and it will go through initial sync.
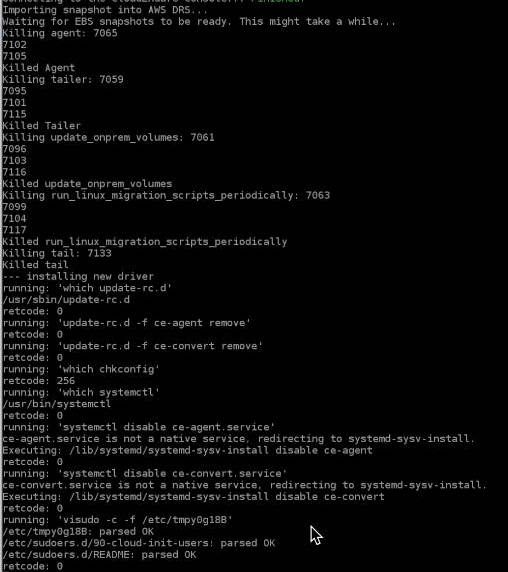
The CECloudEndure agentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. will be uninstalled and the AWS Replication AgentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. will be enabled.
The agentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. will now be active and will start to replicate.
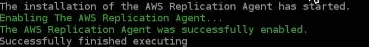
Note: RPO will be briefly affected during this process.
You will still be able to see the machineA physical or virtual computer. in the CECloudEndure console, it will be in a new state called Replicating with AWS Elastic Disaster Recovery. You will not be double billed for replication during this time.
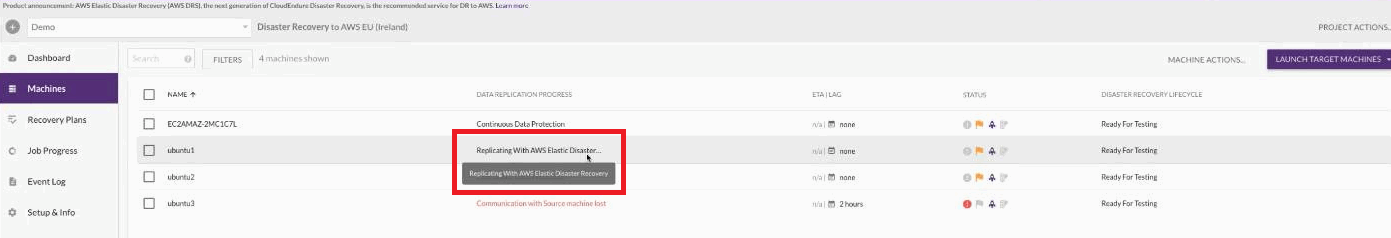
You can still launch TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). machines in CEDR during this time. You can use snapshots that are retained, but no new snapshots will be saved in CEDR. If you experience a disaster during the upgrade, you will still be able to launch TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). machines from CEDR from retained snapshots, but all new snapshots will be taken in DRS.
Once rescan is complete, the machineA physical or virtual computer. will reach the Ready for recovery status and you will see your snapshots in DRS as they populate over time based on your DRS Point-in-time retention settings.
Important: You will still be billed for the snapshots held in CEDR during the retention period.
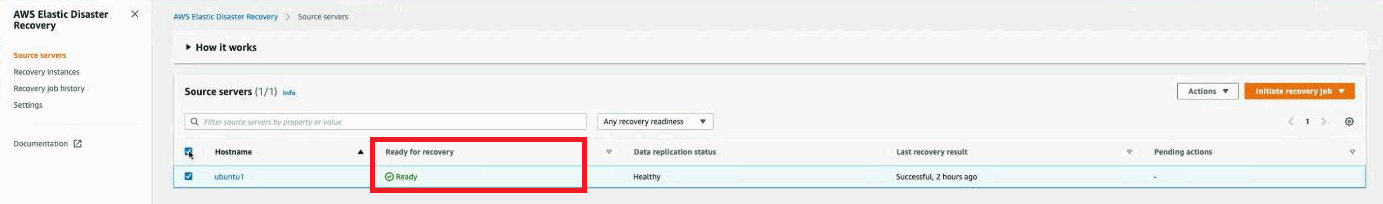
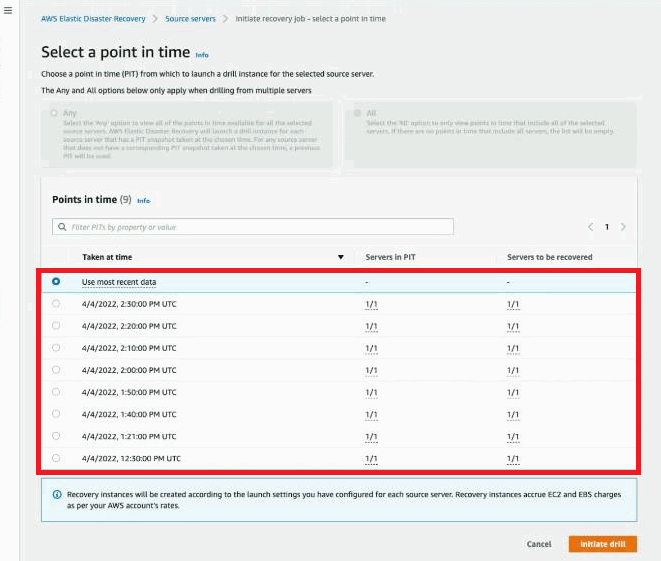
Your source server will now be a part of DRS and you will be able to launch Drill and Recovery instances as per regular operations. Learn more about configuring and using DRS in the DRS documentation.
Once you have successfully upgraded all of your servers from CEDR to DRS and the servers have reached the PITPoint In Time recovery. The ability to restore a Machine to its state in one of the many Points In Time in the past (a feature related to DR). retention period, you can delete your CEDR AccountThe entity that signed up with CloudEndure..
If the assessment tool warns about RecoveryInstance permissions, make sure the role associated with the blueprint also has the permissions specified in the managed policy AWSElasticDisasterRecoveryRecoveryInstancePolicy. Note that the assessment tool cannot verify which policy is attached to the role specified in the blueprint, so the warning will still be reported by the tool even if the role has these permissions.
©2021 COPYRIGHT CloudEndure - Terms of Service - Privacy Policy - AWS Vulnerability Reporting Guidelines - Report a Security Issue