pn fant
Solving Communication Problems over Port 1500
Important! The information provided in this section is for general Troubleshooting guidance only. The information is provided on "AS IS" basis, with no guarantee of completeness, accuracy or timeliness, and without warranty or representations of any kind, expressed or implied. In no event will CloudEndure and/or its subsidiaries and/or their employees or service providers be liable to you or anyone else for any decision made or action taken in reliance on the information provided above or for any direct, indirect, consequential, special or similar damages (including any kind of loss), even if advised of the possibility of such damages. CloudEndure is not responsible for the update, validation or support of troubleshooting information.
To solve connectivity problems between machines and the , check the following:
- [For AWS only] The Network ACL on the subnet may deny the traffic.
- Route Rules on the subnet may be inaccurately set.
- The firewall, both internal and external, in the /infrastructure may block communication.
- The Use VPN... checkbox in CloudEndure may not be set correctly.
Enabling the Network ACL
The Network ACL on the subnet may block connectivity. By default, the Network ACL allows connectivity. However, if the ACL setting was changes to deny traffic, you need to change it back.
To check and enable the network ACL on the subnet:
- Sign in to the AWS console, click on Services and select VPC under Networking & Content Delivery.

- On the Resources list, select the Network ACL option:
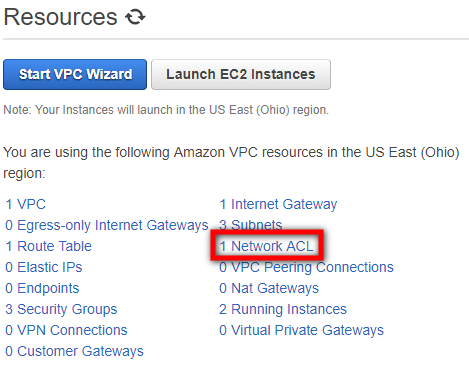
- On Network ACL page, select the check box next to the Network ACL of your .

- On the details table of the selected Network ACL, select the Inbound Rules tab.
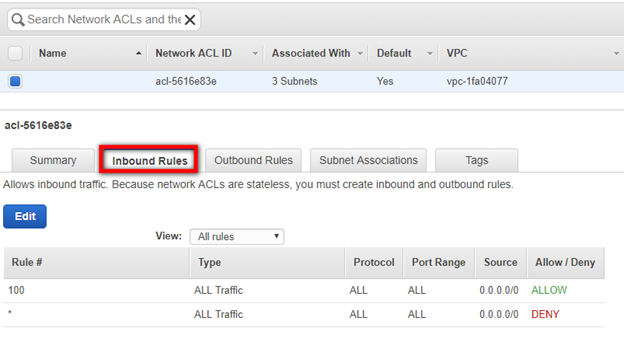
- On the Inbound Rules tab, verify that the Rule that determines the traffic to subnet set to Allow.
Note: The Target should allow traffic on TCP Port 1500 from the address space of the Source environment. The Network ACL does not necessarily need to be open to all Port Ranges, as in the screenshot below.
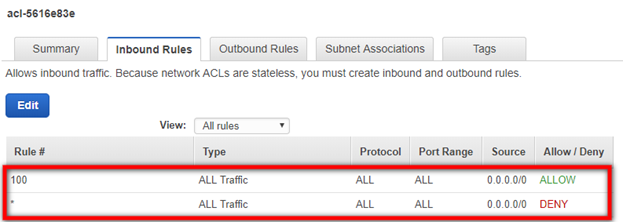
- If the rule is set to Deny, click on the Edit button.
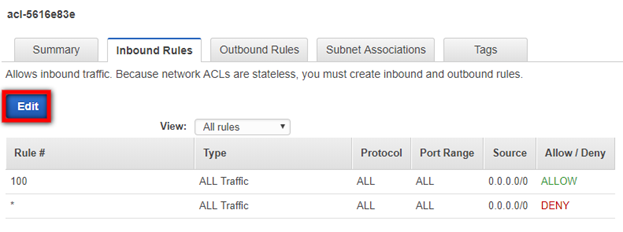
- Click the dropdown under Allow/Deny and select Allow. Click Save.
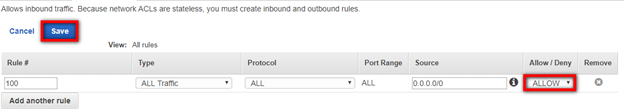
You will also need to check the Ephemeral Ports on the Outbound Rules tab. Within the same Network ACL, navigate to the Outbound Rules tab.
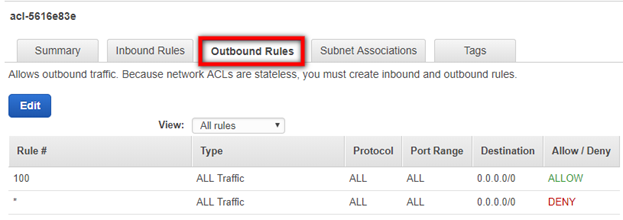
You will need to ensure that you are allowing the correct Ephemeral Port range for your particular client. Ephemeral Port range varies based on each client's operating system. Click the Edit button to edit your Ephemeral Port's Port Range category.
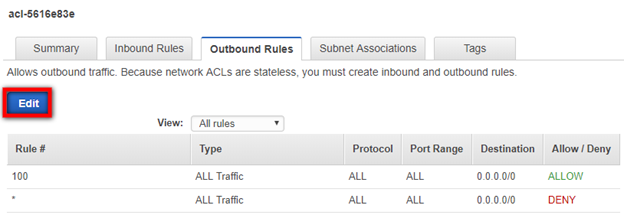
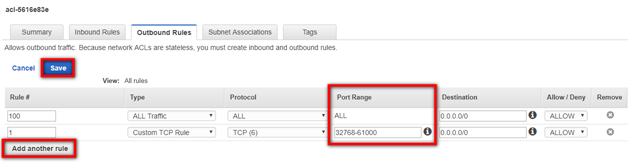
Edit the Port Range and click Save. You may have to create a new Rule by clicking the Add another rule button.
Setting Route Rules on the Staging Area Subnet
AWS
To check and set the Route Rules on the subnet in AWS:
- Sign in to AWS console, click on Services and select VPC under Networking & Content Delivery.
- On the VPC Dashboard toolbar, select the Route Tables option.
- On theRoute Tables page, check the box of the Route Table of your Network .
- This will open the details for your Route Table. Navigate to the Routes tab.
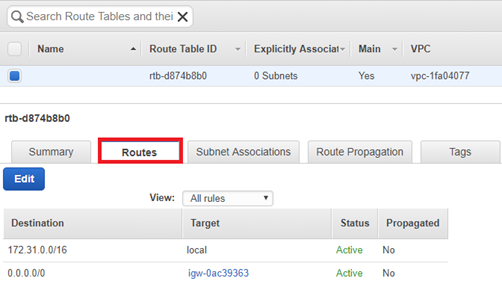
- Within the Target column of the Routes tab, find the route you are using for the inbound traffic from the Source on TCP Port 1500 (either igw - Internet Gateway, vgw - VPN or i – EC2 instance). Verify that the Destination address is 0.0.0.0/0.
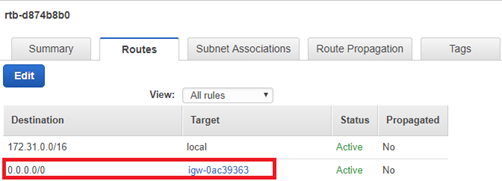
Note: The Rule may be specific to the address space of the Source machines.
- If the address is not 0.0.0.0/0, you will need change it to 0.0.0.0/0.
Note: The Rule may be specific to the address space of the Source machines.
- Click the Edit button.
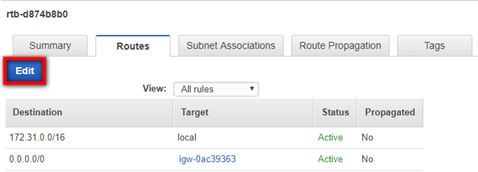
- Input 0.0.0.0/0 into the Destination field for the correct . Click Save.
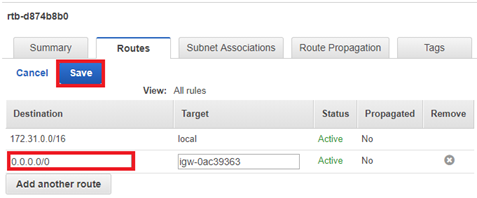
Note: If you are using VPN, enter a specific IP address range in the Destination column.
Firewall (both internal and external) in the Source machine/infrastructure.
Firewall issues may have several causes. Check the following if you experience any firewall issues, such as Windows Firewall connection issues:
- All platforms
- Ensure that the subnet you assigned for the still exists.
- AWS
- Ensure that you have selected a specific subnet in Setup & Info > Replication Settings if you do not have a default VPC or if your AWS account is a EC2-classic account.
Setting the Use Private Connection Checkbox
You can access the Use VPN… checkbox by navigating to Setup & Info > Replication Settings within your project.
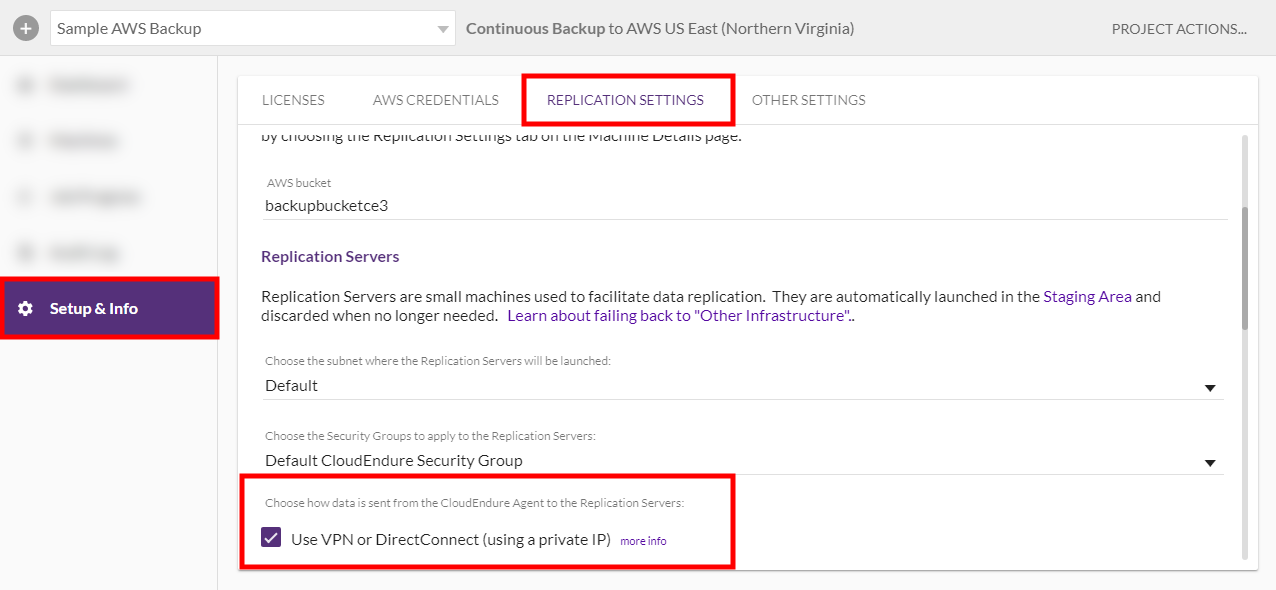
Check this checkbox if you want the replicated data to be transmitted from the to the over a private connection.
Note: You can only use this option if you already have a VPN connection. Selecting this checkbox will not create a new private connection. You should use this option if you want to:
- Allocate dedicated bandwidth for the replication
- Use another level of encryption
- Add another layer of security by transferring the replicated data from one private IP address (Source) to another private IP address (Target).
You can safely switch between a private connection and a public one, by checking or unchecking the Use VPN… checkbox, even after the replication has started. This switch will only cause a very short pause in the replication, and will not have any long-term effect on the replication.
©2020 COPYRIGHT CloudEndure - Terms of Service - Privacy Policy - AWS Vulnerability Reporting Guidelines - Report a Security Issue



















