
Important! The information provided in this section is for general Troubleshooting guidance only. The information is provided on "AS IS" basis, with no guarantee of completeness, accuracy or timeliness, and without warranty or representations of any kind, expressed or implied. In no event will CloudEndure and/or its subsidiaries and/or their employees or service providers be liable to you or anyone else for any decision made or action taken in reliance on the information provided above or for any direct, indirect, consequential, special or similar damages (including any kind of loss), even if advised of the possibility of such damages. CloudEndure is not responsible for the update, validation or support of troubleshooting information.
During replication you may see a server falls out of Continuous Data Protection (CDPA method of replicating data in real time from one location to another. CDP works by capturing every change to any block on a storage volume in real time, and sending it immediately to a remote location. Traditional enterprise-grade disaster recovery solutions, such as the ones provided by IBM, EMC, NetApp and Microsoft all use CDP for storage or hypervisor replication.) mode. This may occur for various reasons, typically related to the network throughput or interruption.
Note: The following instructions demonstrate how to run a speed test through the iperf3 utility for both Linux and Windows. However, we strongly recommend utilizing the SSL Connectivity and Bandwidth test.
The replication speed depends on 4 key factors:
To test your uplink speed, you can you utility such as the iperf3 utility as follows:
Note: If you're using Red Hat/CentOS use yum install instead. Note that epel-release package may be required.
iperf3 -s -p 1500Note: We recommend using the SSL Connectivity and bandwidth test for Windows instead of iperf.
iperf3.exe -i 10 -c Vanilla_linux_server_ip -p 1500 -t 60 > iperf60.logiperf3.exe -i 10 -c Vanilla_linux_server_ip -p 1500 -t 1800 > iperf1800.log
oriperf3 -i 10 -c Vanilla_linux_server_ip -p 1500 -t 60 > iperf60.logiperf3 -i 10 -c Vanilla_linux_server_ip -p 1500 -t 1800 > iperf1800.log
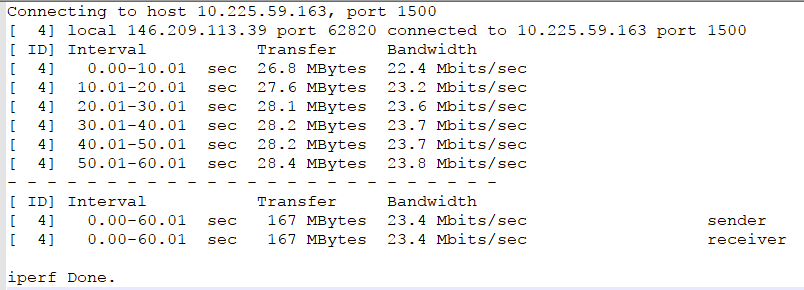
Here is a sample output:

In this output, you can see that the uplink is 23.4Mbps which means that a 100GB (idle) server should be replicated in about 10 hours. You can use this calculator, for example.
Note, if your server writes to disk an average of 20GB/day you need to take it into account when calculating as follows: 20GB/day --> ~2Mbps --> which leave us with only 21.4Mbps available for the initial 100GB.
Note: This tool is for AWS only.
You can use our SSL bandwidth tool to check for replication bandwidth availability.
1. In your TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). region, launch an m4.large test server using the public AMI named CE-ssl-speedtest.
.png)
2. Select the same Subnet as the Subnet used in the Replication SettingsIn the Console UI, a set of settings affecting the data replication process, including Replication Servers subnet and IP, data throttling, use dedicated replicator, use multiple connections, etc. of your Source machineThe computer, physical or virtual machine that needs to be protected by replication (Disaster Recovery) or migrated (Migration) The CloudEndure Agent is installed on the Source machine..
3. Make sure that the Security GroupThe Security Group is an AWS feature that acts as a virtual firewall, which controls the inbound and outbout traffic of the Staging area. allows TCP Port 1500 inbound access.
https://<test_server_ip>:1500/speedtest
5. Click on the Start button.
Note: Browse to the web page using the test server public or private IP according to what you set in your Replication Settings.
Note: The following are the AMI details per region.
ami-033a4924b13126a7b - Oregon
ami-00b38c08ab3506ea7 - N. Virginia
ami-00b7159e9c985a8da - N. California
ami-0bd8423a4d80563fc - Ohio
ami-0edd5ecfc56804583 - Sao Paolo
ami-0a3f9008725d0b4d1 - Paris
ami-097fb47f3a1c2bf7e - London
ami-0dd5a09d2ae8f46b3 - Ireland
ami-07b7defb87a46bb48 - Frankfurt
ami-01c24408802db503d - Canada central
ami-04e7cc6b5d9e8ffa1 - Sydney
ami-0afd42552b236f9dd - Singapore
ami-0b1aeb50834102c18 - Mumbai
ami-08b042df0d4c458ea - Seoul
ami-044fa8034a31d7578 - Tokyo
ami-0971e46306691cd68 - Osaka-Local
ami-0b8643189a66159c9 - Stockholm
ami-0bf60b09675c8d9b6 - Cape Town
ami-0f01375b50763621b - Hong Kong
ami-02f31943dfd88549d - Jakarta
ami-0c65965703bb0e541 - Milan
ami-0c90e298af7a2e563 - Bahrain
Note: Ensure that the Security Group are configured to permit connectivity on inbound port 1500.
The replication steps are the following (the steps involved in the automatic creation of a Replication ServerThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location. in the Staging AreaA part of the Target location; includes the Replication Servers’ subnet, IPs, and the Replication Servers and their disks., over TCP Port 1500)
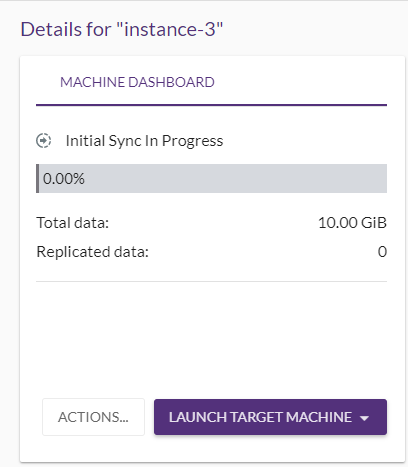
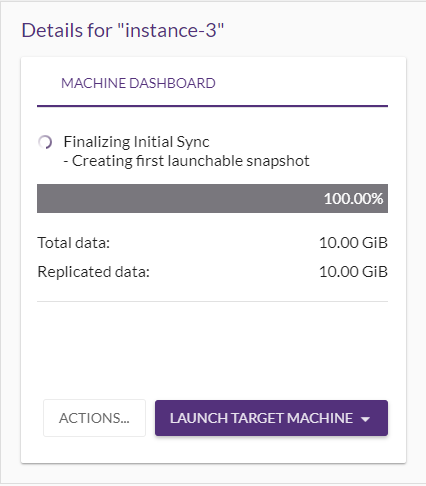
Once communication is established between the AgentThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. and the Replication ServerThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location., Data ReplicationThe process of copying all data blocks from selected disks on a Source Machine to Staging Disks. begins. The following are the Data ReplicationThe process of copying all data blocks from selected disks on a Source Machine to Staging Disks. steps:
.png)
You can start, stop, and pause Data ReplicationThe process of copying all data blocks from selected disks on a Source Machine to Staging Disks. from the right-hand MACHINE ACTIONS menu within the Machines tab. 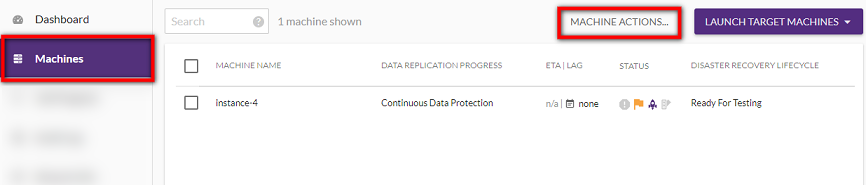
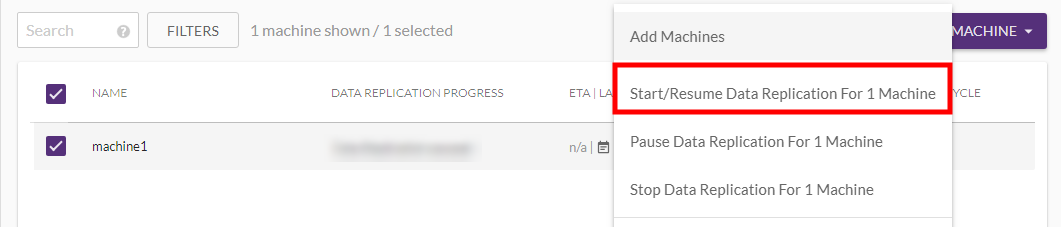
CloudEndure encrypts all the data in transit.
CloudEndure provisions the Replication ServerThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location.(s) and automatically manages the addition and removal of the servers as necessary.
CloudEndure utilizes low cost storage in the Staging AreaA part of the Target location; includes the Replication Servers’ subnet, IPs, and the Replication Servers and their disks..
AWS
CloudEndure utilizes EBS for CloudEndure MigrationThe CloudEndure solution that allows you to move data, applications, and other business elements from an onsite network or a cloud environment to another physical location or cloud environment. and Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event..
For MigrationThe CloudEndure solution that allows you to move data, applications, and other business elements from an onsite network or a cloud environment to another physical location or cloud environment. & Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event., EBS magnetic is utilized for volumes less than "<" 500GiB. For volumes greater than ">" 500GiB, CloudEndure utilizes GP2, GP3 or ST1, depending on the disk type. The typical ratio of volumes to replication serversThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location. is 15:1 for MigrationThe CloudEndure solution that allows you to move data, applications, and other business elements from an onsite network or a cloud environment to another physical location or cloud environment. & Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event..
AWS
CloudEndure provisions a t3.Small server for MigrationThe CloudEndure solution that allows you to move data, applications, and other business elements from an onsite network or a cloud environment to another physical location or cloud environment. and Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event. replication. The typical ratio of volumes to replication serversThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location. is 15:1 for MigrationThe CloudEndure solution that allows you to move data, applications, and other business elements from an onsite network or a cloud environment to another physical location or cloud environment. & Disaster RecoveryThe CloudEndure solution that enables the recovery or continuation of vital technology infrastructure and systems in case of a crippling event..
Yes, CloudEndure utilizes LZW compression during transit resulting in 60-70% compression depending on the type of data.
Yes, CloudEndure generates standard AWS API calls that are visible in CloudTrail.
You will need to confirm that you are filtering on the CloudEndure IAM user in CloudTrail.
For each disk, there are two groups of snapshots:
There is currently no mechanism for users to adjust the frequency and number of snapshots.
CloudEndure automatically deletes snapshots and staging volumesThe disks attached to the Replication Servers that are no longer used (such as those left over after SourceThe location of the Source machine; Currently either a specific Region or Other Infrastructure. machines have been removed from the User ConsoleCloudEndure SaaS User Interface. A web-based UI for setting up, managing, and monitoring the Migration and Disaster Recovery solutions..)
A volume is created for each volume in the SourceThe location of the Source machine; Currently either a specific Region or Other Infrastructure. infrastructure of the same size.
CloudEndure uses TCP Port 1500 for replication between the SourceThe location of the Source machine; Currently either a specific Region or Other Infrastructure. AgentsThe Agent is a software program that is installed on machines in the Source location that need to be migrated or replicated to the Target location. and the Replication ServerThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location.. The connection is open for all IPs and can be managed by ACLs or networks controls to limit inbound IPs.
Replication of Oracle with ASM is supported. CloudEndure replication works directly on block devices and not on mounts. ASM volumes are presented as block devices and therefore replicated transparently by CloudEndure.
By default, CloudEndure does not support use of Oracle ASM Filter Driver. The servers will appear to be in CDPA method of replicating data in real time from one location to another. CDP works by capturing every change to any block on a storage volume in real time, and sending it immediately to a remote location. Traditional enterprise-grade disaster recovery solutions, such as the ones provided by IBM, EMC, NetApp and Microsoft all use CDP for storage or hypervisor replication., but the data will not actually replicate. Support for Oracle ASM Filter Driver for Oracle Database 12c and 19c is available for RHEL7 only, using an installation flag. This flag requires rebooting the server after installation. For specific instruction please reach out to Support.
The Data Replication Progress status bar should show Continuous Data Protection and LagA delay between the changes that occur on the Source and the replication of that changes to the Target. Lag appears when replication does not occur for a certain period of time. should be None.
A rescan may occur after a reboot of the Source machineThe computer, physical or virtual machine that needs to be protected by replication (Disaster Recovery) or migrated (Migration) The CloudEndure Agent is installed on the Source machine.. The rescan time will vary depending on the size of the SourceThe location of the Source machine; Currently either a specific Region or Other Infrastructure. disks. The time depends on the performance of the disks (linear read), target disksThe disks attached to the Target machines. (linear read), and the rate of write operations on the Source machineThe computer, physical or virtual machine that needs to be protected by replication (Disaster Recovery) or migrated (Migration) The CloudEndure Agent is installed on the Source machine. (which are sent in parallel with the re-scan.) The re-scan is functioning normally as long as its moving forward and is not "stuck".
Note: A rescan usually only occurs after a graceful reboot in a Linux environment. During the rescan, all contents of the disk will be read to ensure that no changes were made to the disk. During the read time, RPO and Lag experienced may grow - the larger the disk, the larger the RPO and Lag.
Yes, CloudEndure is crash-consistent.
Replicating your Cluster nodes can be done in one of the following ways:
Option A
Option B
CloudEndureVolumeUpdater service.Option C
CloudEndureVolumeUpdater service.The Volume Updater service is responsible for:
When replicating Clusters, the disks may be detached from the machineA physical or virtual computer. temporarily when the cluster fails over, and therefore disabling that service is recommended.
When the VolumeUpdater service is disabled, note:
You can set the Replication ServerThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location. IP address range by using a VPN connection to determine the IP addresses within your internal network. Ensure that you have already set up a VPN connection in the AWS Console prior to enabling this setting within the Replication SettingsIn the Console UI, a set of settings affecting the data replication process, including Replication Servers subnet and IP, data throttling, use dedicated replicator, use multiple connections, etc. tab in the CloudEndure User ConsoleCloudEndure SaaS User Interface. A web-based UI for setting up, managing, and monitoring the Migration and Disaster Recovery solutions..
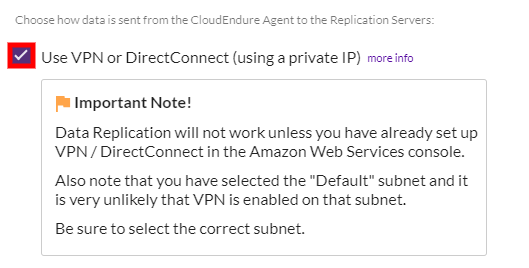
No, you can only replicate to a single TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery). at once with CloudEndure. To replicate to multiple TargetsThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery)., you will have to create multiple ProjectsA Project is the basic organizational unit for running a CloudEndure solution. - one for each TargetThe location where the Replication Server will be located and where Target machines will be created (as a result of Test, Cutover or Recovery)..
Yes.
This means that the machineA physical or virtual computer. has been experiencing lagA delay between the changes that occur on the Source and the replication of that changes to the Target. Lag appears when replication does not occur for a certain period of time. for longer than 48 hours.
When migrating Linux machines into AWS with CloudEndure, all licenses are BYOL. Any RHEL, SUSE or Debian licenses will be transferred in their current form to the migrated machineA physical or virtual computer.. The customer is responsibly to ensure that the terms of their licenses allow this license transfer.
When migrating Windows machines into AWS, you can Bring Your Own (BYOL) Windows LicenseAllows the installation of the Agent on one machine. One License enables one Agent. Licenses are a part of the License Package. by setting a Dedicated Host in the machineA physical or virtual computer. Blueprint. When this is done, the licenses from the Source machineThe computer, physical or virtual machine that needs to be protected by replication (Disaster Recovery) or migrated (Migration) The CloudEndure Agent is installed on the Source machine. will be automatically transferred to the Target machineThe Machine created during Test, Cutover or Recovery. in AWS.
Note: For MSDN Windows licenses, you can use the Dedicated Instance option in addition to the Dedicated Host option. Selecting the Dedicated Instance option in the machine Blueprint does not allow Windows BYOL by default. To be able to transfer MSDN Windows licenses over to Dedicated Instances, contact Support.
No. AWS Nitro instances do not support RHEL 5 and 6. Choose XEN-based instances instead.
No. CloudEndure does not currently support replicating EC2 instances that utilize the EBS volume multi-attach feature.
The regular ratio for CloudEndure is 15 disks for each single replication serverThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location.. Any single machineA physical or virtual computer. with more than 15 disks will have its own replication serverThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location.. The disks will not be split into separate replication serversThe CloudEndure Machine to which Staging Disks are attached and to which data is replicated; launched on the Target location..
Starting at end of year 2021, all CloudEndure replication machines’ underlying EC2 instances have been based on Amazon Linux 2 (AL2) AMIs.
These AMIs are periodically upgraded and published in the AMI section of the EC2 service.
Updated AMI images will have different AMI ids (formatted as `ami-0633fb238aabbccdd`) per region, but the same name (example: `amzn2-ami-hvm-2.0.20220606.1-x86_64-gp2`).
Normally only the name field and the sub-version (0/1) '20220606.1' is changed when a new AL2 AMI is published.
CloudEndure periodically detects and upgrades the AMI IDs used to create AL2 based replicator machines.
CECloudEndure AL2 AMIs versions history:
| Date | AMI name |
|---|---|
| Nov 12 2023 | amzn2-ami-hvm-2.0.20231101.0-x86_64-gp2 |
| Aug 27 2023 | amzn2-ami-hvm-2.0.20230628.0-x86_64-gp2 |
| Jan 10 2023 | amzn2-ami-hvm-2.0.20221210.0-x86_64-gp2 |
| Dec 1 2022 | amzn2-ami-hvm-2.0.20221103.0-x86_64-gp2 |
| Nov 6 2022 | amzn2-ami-hvm-2.0.20221004.0-x86_64-gp2 |
| Oct 30 2022 | amzn2-ami-hvm-2.0.20220912.0-x86_64-gp2 |
| Sep 11 2022 | amzn2-ami-hvm-2.0.20220805.0-x86_64-gp2 |
| Aug 2 2022 | amzn2-ami-hvm-2.0.20220719.0-x86_64-gp2 |
| July 31 2022 | amzn2-ami-hvm-2.0.20220606.1-x86_64-gp2 |
| June 9 2022 | amzn2-ami-hvm-2.0.20220426.0-x86_64-gp2 |
©2020 COPYRIGHT CloudEndure - Terms of Service - Privacy Policy - AWS Vulnerability Reporting Guidelines - Report a Security Issue